LinkDaddy Cloud Services - Reinvent Your Business Workflow
Wiki Article
Secure and Scalable Cloud Solutions for Expanding Companies
In a digital landscape where services are continually developing, the value of safe and scalable cloud solutions can not be overemphasized. As companies navigate the complexities of cloud remedies, a deeper understanding of the nuances included is imperative for optimizing their capacity.Advantages of Cloud Provider
Cloud solutions offer a wide range of advantages for companies seeking scalable and cost-efficient options to handle their data and procedures. One key benefit is flexibility; cloud services permit services to conveniently scale their sources up or down based on demand, offering the dexterity required in today's hectic market (Cloud Services). This scalability likewise removes the demand for companies to buy costly on-premises equipment that might swiftly come to be obsoleteOne more advantage of cloud solutions is cost-effectiveness. By utilizing a pay-as-you-go model, companies can prevent big ahead of time investments and only pay for the resources they in fact utilize. This can result in significant expense savings, especially for expanding businesses with varying demands. Additionally, cloud services usually consist of automated software updates and maintenance, decreasing the problem on interior IT groups and making certain that systems are constantly approximately date and secure.
Furthermore, cloud services provide boosted collaboration and ease of access. With information stored in the cloud, workers can conveniently access and service files from anywhere with an internet link, promoting partnership and productivity. On the whole, the benefits of cloud solutions make them an attractive alternative for companies wanting to streamline their procedures and stay competitive in the digital age.
Importance of Security Measures
Making sure robust safety actions is extremely important for organizations utilizing cloud services to secure their delicate data and procedures. With the enhancing dependence on cloud innovation, the requirement for strict safety procedures has actually ended up being much more essential than ever before. Executing protection actions assists in stopping unapproved gain access to, information breaches, and other cyber hazards that could endanger the integrity and confidentiality of business information.Moreover, developing clear safety plans and supplying comprehensive training to workers on finest protection methods can considerably decrease the danger of human error bring about security violations. By buying robust security steps, companies can impart count on among their clients, adhere to information security policies, and minimize prospective financial and reputational damages connected with safety events.
Scalability for Service Growth
Attaining seamless scalability is a basic facet for businesses going for sustained development and development in their operations. Scalability in cloud solutions allows organizations to adjust swiftly to changing demands by easily adjusting sources such as storage space, refining power, and bandwidth. cloud services press release. This versatility is crucial for fitting boosted workloads as services expand, making certain that operations run efficiently without disruptions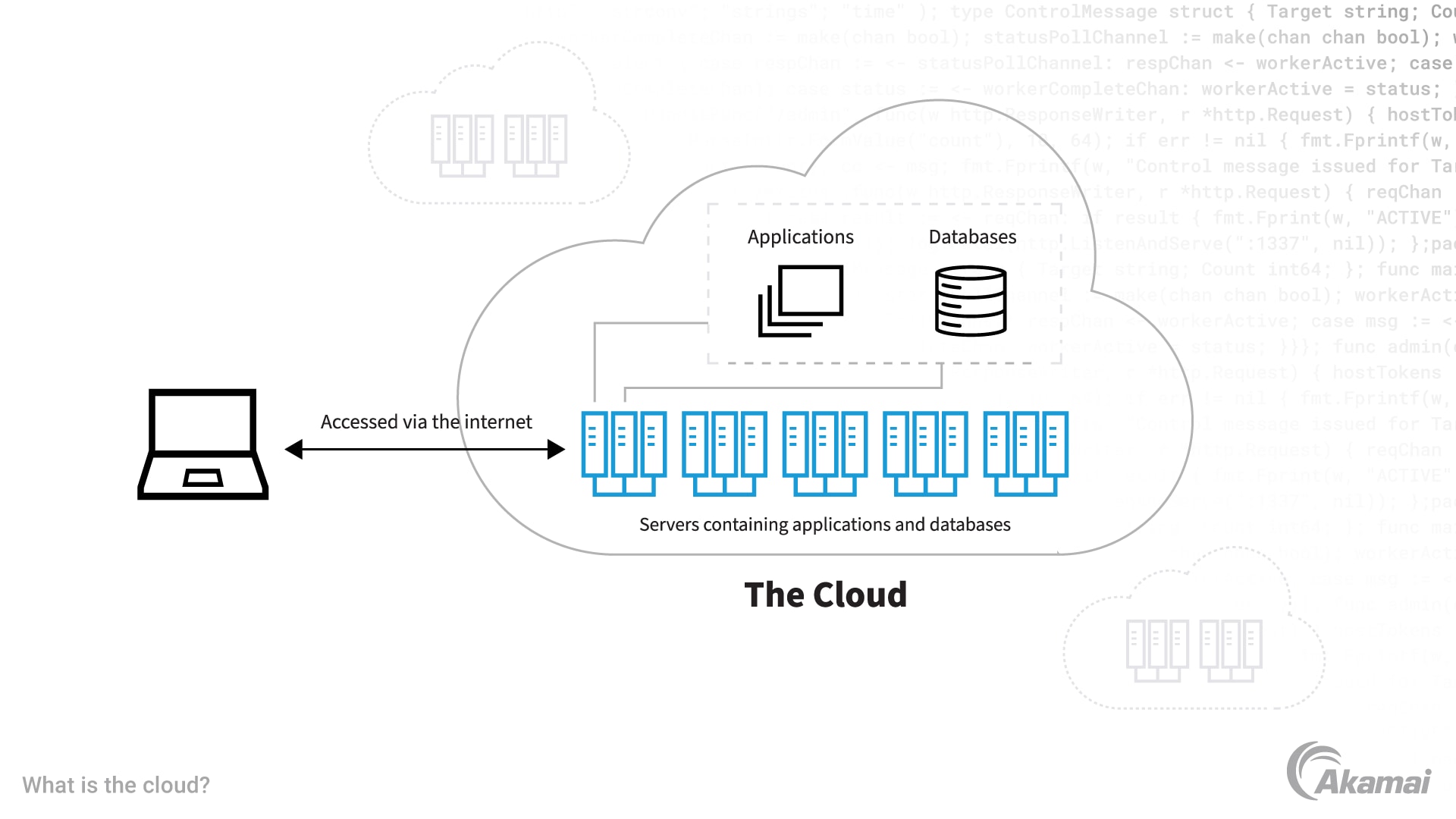
Additionally, scalability cultivates technology by offering the foundation for explore originalities and modern technologies without restrictions. As companies expand and develop, having a scalable cloud framework in place is important for sustaining growth initiatives and taking full advantage of functional performance. By embracing scalable cloud solutions, companies can position themselves for long-term success and lasting development.
Key Attributes for Information Protection
Executing robust data security procedures is vital for securing sensitive information and keeping the stability of organization operations. By securing information, businesses can avoid unapproved access and mitigate the risk of data breaches.Regular data backups are an additional essential attribute for data defense, allowing organizations to recuperate information in case of accidental deletion, cyber-attacks, or system failures. Back-up remedies must be automated, regular, and stored in geographically varied places to make sure data durability. Furthermore, implementing multi-factor authentication adds an extra layer of protection by needing individuals to give multiple forms of confirmation before accessing delicate data. These key features jointly add to a robust data defense method, securing business-critical details in the cloud environment.
Enhancing Business Performance
To optimize operational productivity and streamline processes, companies can utilize various devices and technologies targeted at improving organization effectiveness. One essential aspect of boosting effectiveness is the implementation of cloud-based project monitoring systems. These systems permit smooth collaboration amongst employee, real-time updates on task progression, and centralized record storage. By having all project-related information in one obtainable location, businesses can minimize time thrown away on browsing for records and improve overall performance.Automation tools are an additional essential component for enhancing effectiveness. By automating repetitive jobs such as information entrance, invoicing, and customer interaction, businesses can save beneficial time and allocate resources to more tactical tasks. Furthermore, customer relationship monitoring (CRM) software application can aid services track interactions with clients, handle leads, and improve consumer contentment via individualized communication.
Additionally, adopting cloud-based interaction devices like video conferencing and instant messaging can help with fast decision-making and Cloud Services improve partnership among remote teams. By welcoming these modern technologies, businesses can boost their functional effectiveness and stay competitive in today's busy service setting.
Final Thought
In final thought, secure and scalable cloud services offer essential advantages for expanding organizations by giving information defense, versatility, and effectiveness. By applying strong safety and security actions and making use of the scalability of cloud solutions, firms can adapt to altering demands, innovate, and maintain a competitive edge in the market. It is necessary for companies to prioritize the fostering of protected and scalable cloud services to make certain the protection of their information and facilitate growth.
Report this wiki page